Insights on Human Risk and Enterprise Security
Expert analysis, emerging trends, and the latest product, feature, and company innovations from the team redefining how enterprises think about user risk.

%20(1).avif)
Dune Security and OmegaBlack Partner to Deliver Intelligence-Driven Protection for the User Layer
Threat actors are building their campaigns across the dark web long before they reach the enterprise. Dune Security and OmegaBlack are partnering to deliver layered protection that connects external exposure with user level risk scoring and automated remediation.

Cybersecurity in Healthcare: How Social Engineers Target Patient Data and Hospital Operations
Healthcare’s reliance on digital systems and high-pressure clinical environments has made user risk a patient safety issue, and organizations must rethink how they prepare their workforce for modern attacks.

Dune Security's Revolutionary Approach: AI and Cybersecurity
Dune Security CEO David DellaPelle joins the Cyber Security America podcast to explain how AI-driven social engineering is outpacing traditional security awareness training and why organizations need a behavior-driven approach to identifying and reducing user risk.

Dune Security and Abstract Security Partner to Deliver Real-Time Detection and Automated Risk Reduction
Modern attacks often reveal themselves through subtle technical events that most tools miss until it is too late. Dune Security and Abstract Security now bring real-time detection and automated risk remediation into a single defense strategy.

How a deepfake of Marco Rubio exposed the alarming ease of AI voice scams
An audio deepfake impersonating Secretary of State Marco Rubio contacted foreign ministers, a U.S. governor, and a member of Congress with AI-generated voicemails mimicking his voice, according to a senior U.S. official and a State Department cable dated July 3.

Finance worker pays out $25 million after video call with deepfake ‘chief financial officer’
A finance worker at a multinational firm was tricked into paying out $25 million to fraudsters using deepfake technology to pose as the company’s chief financial officer in a video conference call, according to Hong Kong police.

Dune Security and Reality Defender Team Up at Cooley LLP to Tackle the Rise of Deepfake and Synthetic Media Threats
Deepfakes have emerged as one of the most pressing enterprise threats, capable of eroding trust and triggering costly decisions in seconds. Dune Security and Reality Defender gathered industry leaders at Cooley LLP to explore how organizations can keep up with today’s most advanced threats at scale.

Legacy Security Awareness Training Doesn’t Reduce User Risk
As cyber threats grow more sophisticated, fueled by AI and targeting human behavior, traditional security awareness training is no longer enough. Organizations need a smarter, user-focused approach that not only identifies individual risk but actively reduces it in real time.

Almost 1 billion Salesforce records stolen, hacker group claims
Cybercriminals connected to a recent string of ransomware attacks on major British retailers said on Friday they had stolen almost 1 billion records from cloud technology giant Salesforce, opens new tab by focusing on companies that use its software.

Dune Security Launches Resource Calendar to Help Teams Fight Back This Cybersecurity Awareness Month
Cybercriminals are training every day – but this October, we’re hitting back harder. Our new Resource Calendar helps security teams meaningfully engage employees, strengthen culture, and build resilience all month long.

Dune Security Joins the National Cybersecurity Alliance to Champion Cybersecurity Awareness Month
Dune Security has joined forces with the National Cybersecurity Alliance to champion Cybersecurity Awareness Month. Together, we’re working to strengthen the human layer of cybersecurity and equip employees to stay safe online against modern threats.

CyberVault Podcast: Why Security Awareness Training Fails with David DellaPelle
David DellaPelle, Co-Founder and CEO of Dune Security, joined The CyberVault Podcast to discuss why most security awareness programs fall short and what it takes to build a true human-first security culture.

The Hustle Daily Show: The Billion-Dollar Value of Cybersecurity Startups
David DellaPelle, CEO of Dune Security, joined The Hustle Daily Show to discuss the billion-dollar value of cybersecurity startups, why the industry is booming, and how to break into it.

Cyber Security Matters Podcast: Tackling Social Engineering Prevention
David DellaPelle, Co-Founder and CEO of Dune Security, joined the Cyber Security Matters Podcast to discuss defending against social engineering, the rise of deepfakes, and his journey as a cybersecurity entrepreneur.
Security Architecture Podcast: Securing Tomorrow
David DellaPelle, Co-Founder and CEO of Dune Security, joined the Security Architecture Podcast to discuss Dune’s mission to reduce attack surfaces, counter AI-powered social engineering, and build resilient security cultures.
.jpg)
The ITSM Practice Podcast: Exploring Scattered Spider Cloud Attacks
Tarun Ramesh, Senior Backend Engineer at Dune Security, joined The ITSM Practice Podcast to discuss how Scattered Spider and similar threat groups exploit cloud environments using advanced social engineering and defense strategies.
.jpg)
Inside the Round Podcast: Building Dune Security with David DellaPelle
Dune Security Co-Founder and CEO David DellaPelle joined the Inside the Round Podcast to share how Dune is tackling user risk and what it takes to build a modern cybersecurity company from the ground up.

Dune Security Takes Over Times Square
In less than three years, Dune Security has grown from an idea into a platform trusted by Fortune 1,000 enterprises. Our Times Square milestone celebrates that journey and our mission to stop insider threats and social engineering at scale.

Dune Security and Reality Defender Partner to Stop AI-Generated Media Threats Targeting Enterprises
Deepfakes and AI-generated attacks are targeting employees faster than legacy tools can keep up. Dune Security and Reality Defender are partnering to deliver layered protection against these threats, combining real-time detection with user layer intelligence.

16 billion passwords exposed in record-breaking data breach: what does it mean for you?
Several collections of login credentials reveal one of the largest data breaches in history, totaling a humongous 16 billion exposed login credentials. The data most likely originates from various infostealers.

Former FBI agent thought he had seen it all in cybercrime. Then he became a corporate executive in charge of information security
For cybersecurity workers, 2021 was intense. There was the Russian-based ransomware attack on Colonial Pipeline, a key transit system for U.S. oil, that set off panic-buying at the gas pumps. Meanwhile, major U.S. meat packer JBS was shut down by yet another attack. And then there was the U.S. federal government, which suffered one of its worst cyber espionage breaches ever, due to aftershocks created by the hacking of software maker SolarWinds.
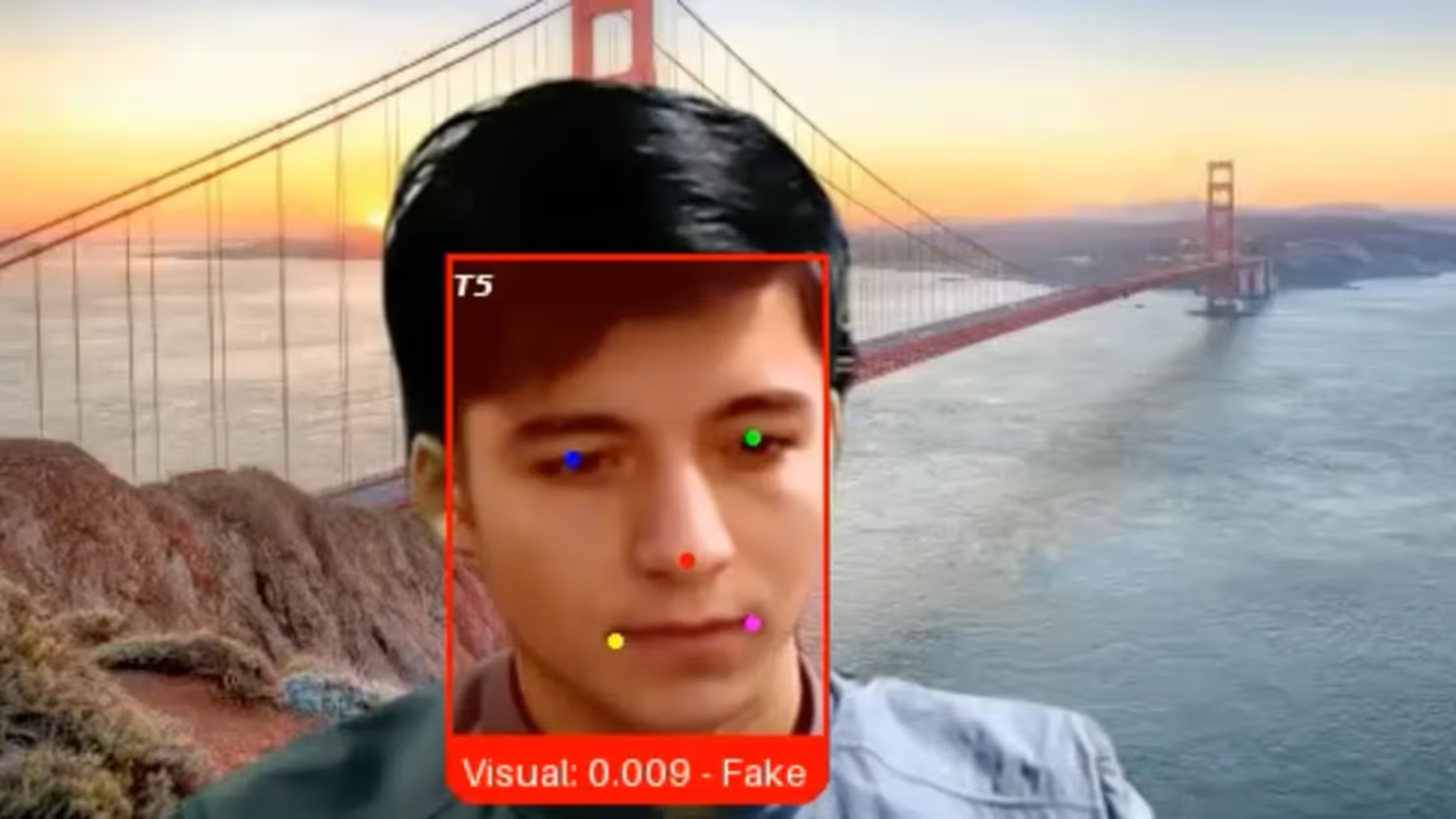
Fake job seekers are flooding U.S. companies that are hiring for remote positions, tech CEOs say
Companies are facing a new threat: Job seekers who aren’t who they say they are, using AI tools to fabricate photo IDs, generate employment histories and provide answers during interviews.

How Ghost Students Are Exploiting College Enrollment Systems to Steal Federal Aid
Criminal fraud rings are targeting college aid systems with fake student identities. These scams use automation, identity theft, and AI to steal financial aid, lock out real students, and overwhelm public institutions. Here’s how it works and what security leaders in higher ed need to know.

How Employee Fatigue Drives Human Error in Cybersecurity
Employee fatigue fuels human error and cybersecurity breaches by creating behavioral blind spots attackers exploit through social engineering and cognitive overload. Replace static awareness training with adaptive, real-time protection built for enterprise-scale risk.
From the Founder
View Linkedin

Never Miss a Human Risk Insights
and strategies for enterprise CISOs.

























%202.avif)







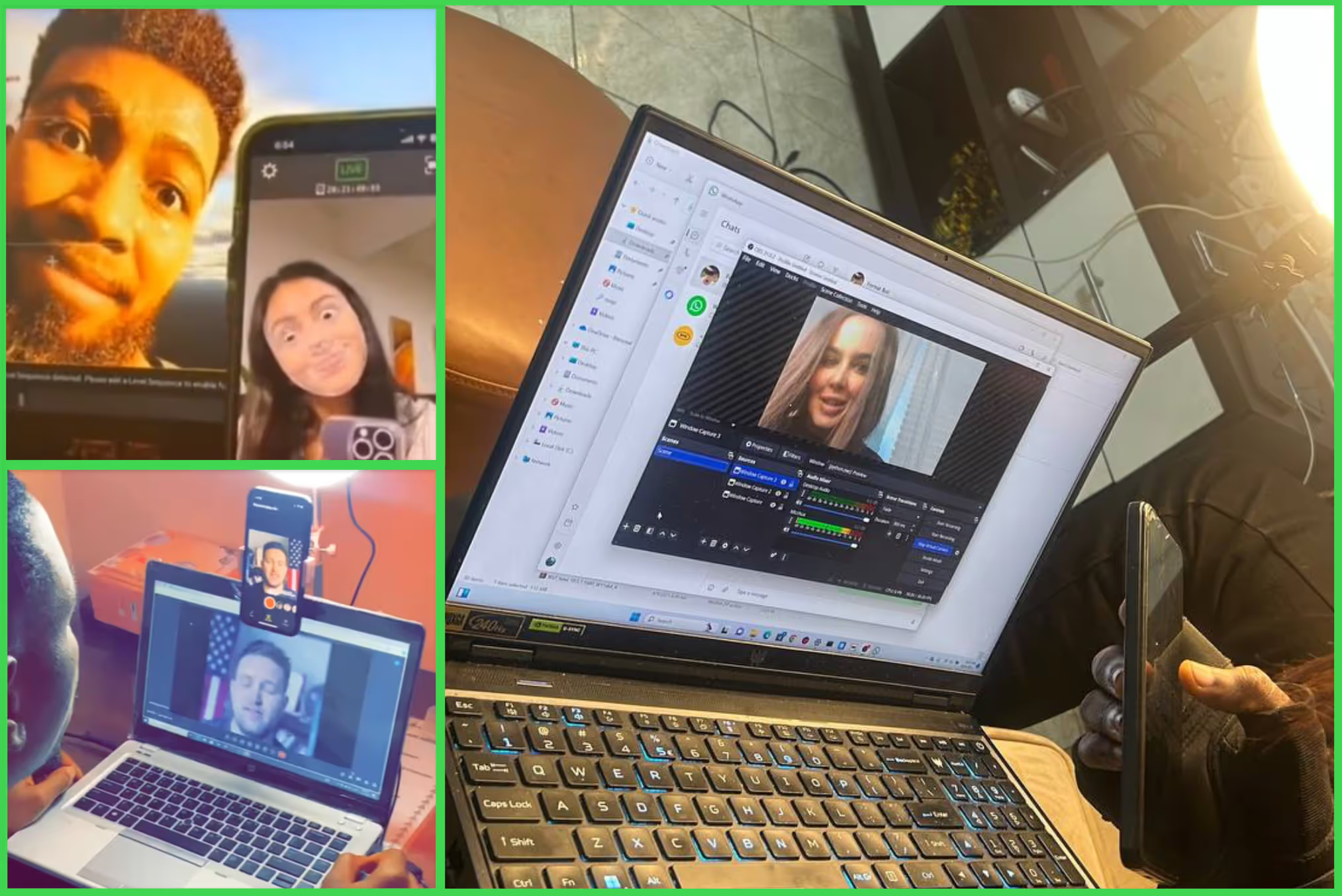



.avif)


