Inside Access
CISOs on the Emerging
Threats Redefining User
Cyber Risk
Built on new data from Dune Security’s 2025 CISO Risk Intelligence Survey and real-world behavioral simulations, this report exposes how attackers are breaching users through multi-channel, AI-powered social engineering, and how these tactics are reshaping enterprise User Layer risk.

.avif)

Why This
Report Matters
Over 90% of breaches begin with user behavior, not malware. Yet most enterprises still test only email-based phishing. This report exposes the gaps between user readiness and real-world threats, and how CISOs are addressing today’s most exploited vectors.
Key Challenges
Encrypted channels are the biggest blind spot in the enterprise
None of the surveyed CISOs simulate attacks via encrypted messaging and only 6% of CISOs express high confidence in their users’ ability to detect threats in WhatsApp or Signal.
AI-personalized phishing is escalating user failure
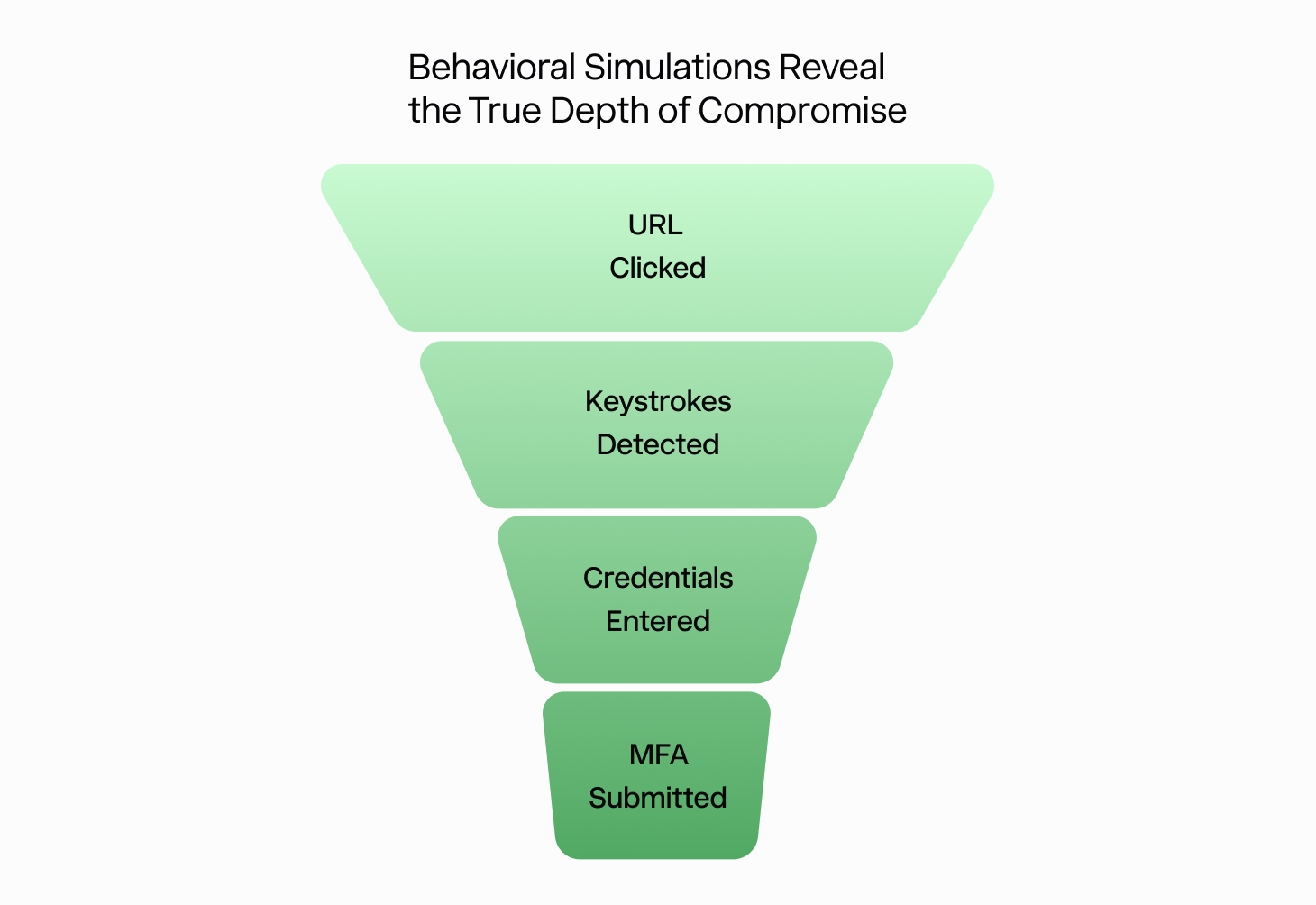
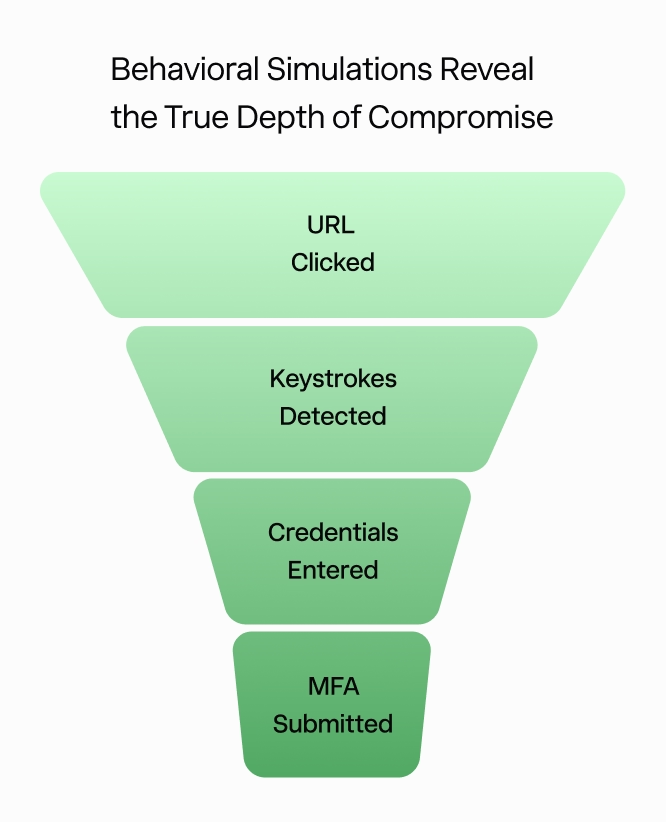
30% of users submitted MFA credentials when tested with realistic phishing simulations, showing how modern attacks drive deeper compromise than legacy templates ever did.
Smishing and vishing remain dangerously under-tested
Only 27% of enterprises simulate SMS-based phishing, and just 15% simulate voice-based deception, despite both being top concerns for CISOs.
Key Stats from the 2025 CISO Risk Intelligence Survey
64%
of enterprises experienced attacks via encrypted or informal channels in the past 12 months
3x
users interact with AI-personalized phishing emails than traditional templates
Only 12%
of CISOs believe their current SAT platform is sufficient
Improve
Training: 26%
Training: 26%
Risk Based
Controls: 29%
Controls: 29%
Other: 6%
Improve
Testing: 21%
Testing: 21%
End-to-End
Visibility: 18%
Visibility: 18%
See How It
Applies to You
Want a deeper look at your own risk surface?
Book a 1:1 session with a Dune strategist to see how these insights align with your user vulnerabilities, exposure gaps, and readiness across real-world attack channels.
Schedule a Personalized Briefing


.avif)
.avif)