Red Team Attack Simulations
Prepare for real-world threats with advanced simulations and measurable user responses.


Most organizations don’t know how their employees would respond under real attack conditions. Without continuous, realistic simulations, critical user-driven vulnerabilities remain hidden, leaving your systems exposed to modern adversary tactics.


How Dune Solves It
Factor in each user’s title, department, access scope, and role sensitivity to prioritize risk based on business exposure.
Launch user-adaptive phishing, smishing, deepfake, and encrypted-channel simulations to test real-world susceptibility.
Track comprehension, completion, and retention of training personalized to each user’s behavior, role, and risk level.
Detect early signs of fatigue, misuse, or compromise by analyzing login failures, unusual access, policy breaches, and drift across IAM, SEG, EDR, DLP, and HRIS systems.
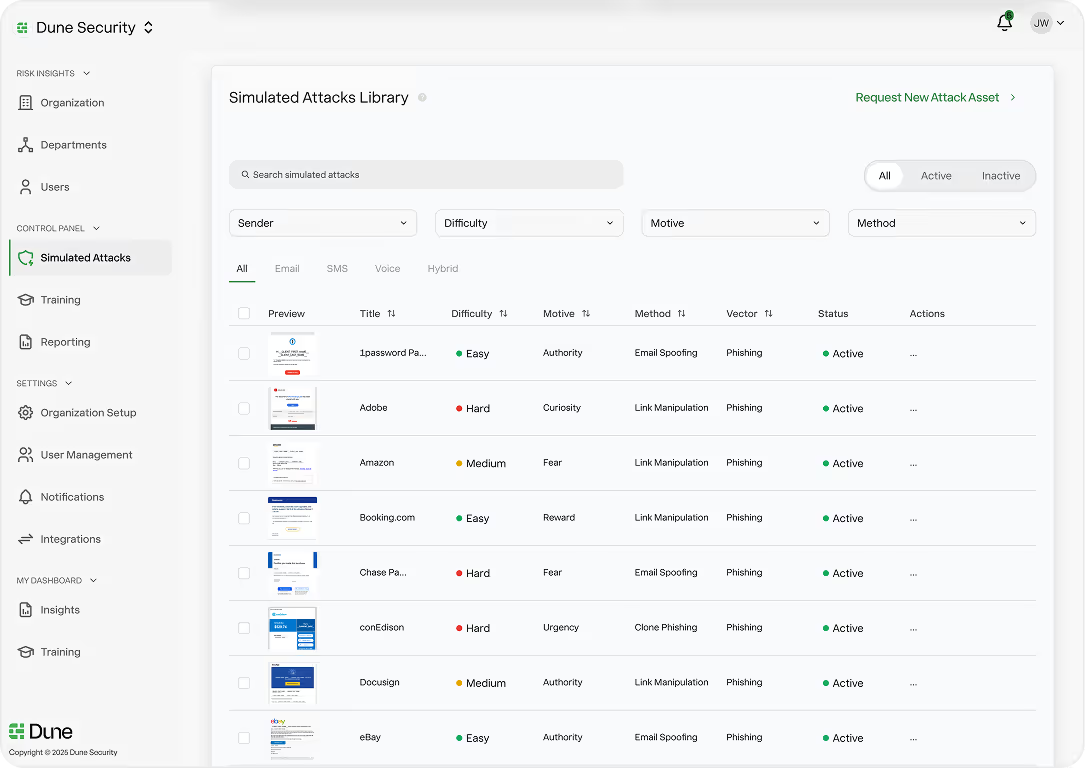
Advanced Threat Emulation
Simulates multi-stage, adversary-style attacks that reflect real kill chains, testing user detection and response at every layer.


Behavioral Response Analytics
Tracks how users interact with simulated threats: clicks, replies, MFA prompts, and credential entries to enrich live risk scoring.


Hybrid Attack Simulation
Simulates chained threat sequences, like a vishing call followed by a phishing payload to assess how users respond to multi-vector attacks.

Enterprise Impact

Identify high-risk user behavior before adversaries exploit it.

Prepare your workforce for real-world cyber threats with realistic, role-specific attack drills.
Automate simulation, feedback, and scoring to build resilient user behavior and measure readiness over time.
Ready to test and strengthen your organization's cyber defenses?
Book a demo

